In the realm of cybersecurity, the use of Effective IT automation tools is paramount for safeguarding against evolving threats. This article delves into the significance of automation in fortifying cybersecurity measures, exploring key tools, benefits, features, and best practices. Brace yourself for a journey into the realm of IT automation for cybersecurity.
Overview of Effective IT Automation Tools for Cybersecurity
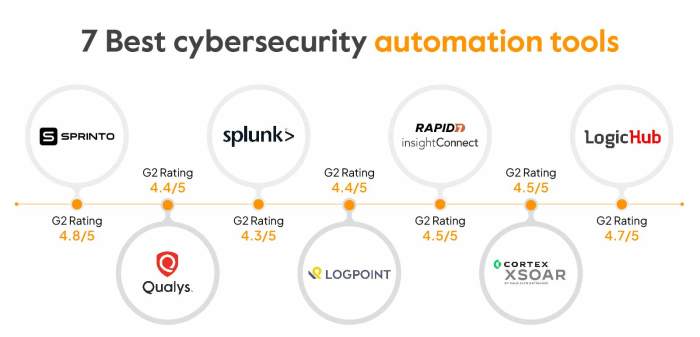
IT automation tools in the context of cybersecurity refer to software solutions that streamline and automate various security tasks and processes within an organization's IT infrastructure. These tools are designed to reduce manual intervention, improve efficiency, and enhance the overall security posture of an organization.
Automation is crucial for enhancing cybersecurity measures due to the increasing complexity and volume of cyber threats faced by organizations. Manual security processes are often time-consuming, error-prone, and may not keep up with the speed at which cyber threats evolve.
By automating routine tasks such as patch management, threat detection, and incident response, organizations can respond to threats more effectively and efficiently.
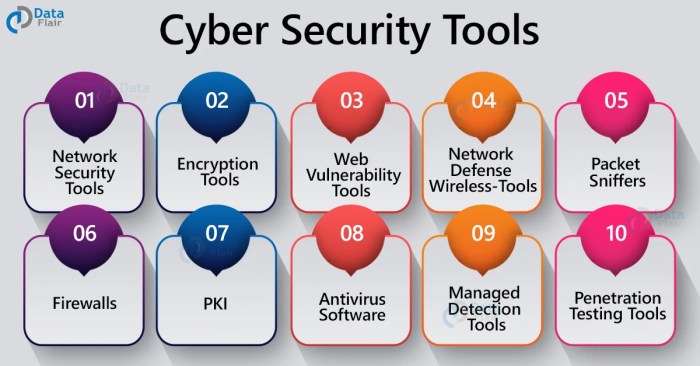
Common IT Automation Tools for Cybersecurity
- Security Information and Event Management (SIEM) tools: SIEM tools collect and analyze security data from various sources to detect and respond to security incidents.
- Vulnerability Management tools: These tools scan networks and systems for vulnerabilities, prioritize them based on risk, and facilitate the remediation process.
- Identity and Access Management (IAM) solutions: IAM tools automate user provisioning, access control, and authentication processes to ensure secure access to resources.
- Security Orchestration, Automation, and Response (SOAR) platforms: SOAR platforms integrate security tools and workflows to automate incident response and threat intelligence processes.
Benefits of IT Automation in Cybersecurity
Automation plays a crucial role in enhancing cybersecurity by streamlining processes, reducing human error, and improving incident response. Let's delve into the specific benefits of IT automation in cybersecurity.
Enhanced Incident Response
Automation tools can significantly improve incident response time in cybersecurity. By automatically detecting and responding to security threats, organizations can mitigate risks more efficiently. For example, automated alert systems can immediately notify security teams of suspicious activities, enabling them to take prompt action to prevent potential breaches.
Reduced Human Error
Human error is a common factor in cybersecurity incidents. IT automation helps minimize the impact of human mistakes by standardizing processes and eliminating manual intervention in routine tasks. By automating repetitive tasks such as patch management and system updates, organizations can reduce the likelihood of errors that could compromise security.
Streamlined Security Processes
IT automation tools can streamline security processes by automating tasks such as vulnerability scanning, compliance checks, and access controls. For instance, automated tools can continuously monitor network traffic for anomalies, ensuring timely identification of potential threats. By automating these processes, organizations can improve overall security posture and operational efficiency.
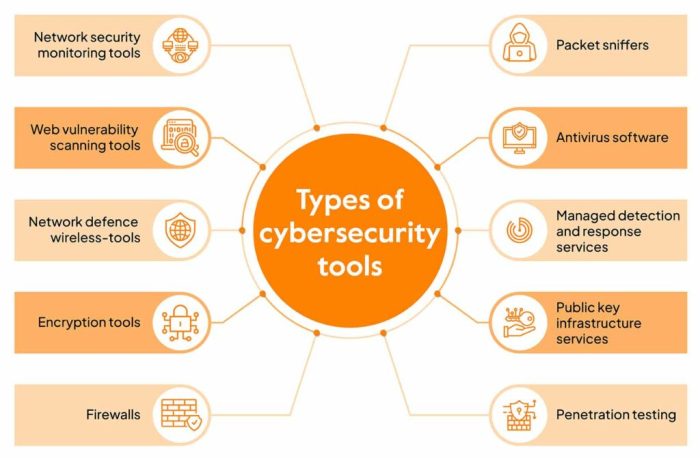
Features to Look for in IT Automation Tools for Cybersecurity
When considering IT automation tools for cybersecurity, it is crucial to assess the key features that make these tools effective in enhancing security operations. The following features play a vital role in determining the efficiency and reliability of IT automation tools in cybersecurity.
1. Integration Capabilities
Effective IT automation tools should have seamless integration capabilities with existing security systems and protocols. This ensures smooth communication and coordination between different security tools and processes, enabling holistic cybersecurity management.
2. Customization Options
Look for automation tools that offer flexible customization options to tailor security workflows according to specific organizational requirements. Customizable automation tools allow security teams to adapt and optimize processes based on evolving threats and vulnerabilities.
3. Scalability and Flexibility
Scalability is essential in IT automation tools to accommodate the growing needs of cybersecurity operations. Tools that can scale up or down based on the organization's requirements ensure efficient resource utilization and adaptability to changing security landscapes.
4. Reporting and Analytics
Comprehensive reporting and analytics features are crucial for monitoring and evaluating the effectiveness of security automation processes. Look for tools that provide detailed insights and metrics to assess the impact of automation on cybersecurity posture.
5. Workflow Orchestration
IT automation tools with advanced workflow orchestration capabilities help streamline security processes and ensure efficient task management. Automated orchestration of security workflows minimizes manual intervention and accelerates incident response times.
6
. Compliance Management
Choose automation tools that offer robust compliance management features to ensure adherence to regulatory requirements and industry standards. Automated compliance checks and reporting functionalities help maintain a secure and compliant IT environment.
7. Threat Intelligence Integration
Integrating threat intelligence feeds into automation tools enhances the ability to proactively detect and respond to emerging threats. Look for tools that support seamless integration with threat intelligence platforms to strengthen cybersecurity defenses.
8. User Access Controls
Effective IT automation tools should provide granular user access controls to restrict unauthorized access and enforce security policies. Role-based access permissions ensure that only authorized personnel can execute critical security automation tasks.
9. Support and Training
Consider automation tools that offer comprehensive support services and training resources to assist security teams in effectively utilizing the tool's capabilities. Access to training materials and expert guidance can help maximize the benefits of IT automation in cybersecurity operations.
Implementation Best Practices for IT Automation in Cybersecurity
Implementing IT automation tools in cybersecurity requires careful planning and execution to ensure a seamless transition and optimal effectiveness. Here are some best practices to consider:
Integrating IT Automation Tools into Existing Cybersecurity Infrastructure
- Conduct a thorough assessment of your current cybersecurity processes and identify areas that can benefit from automation.
- Select automation tools that are compatible with your existing systems and can easily integrate without causing disruptions.
- Develop a detailed implementation plan that Artikels the steps involved in integrating the automation tools, including testing and validation processes.
- Train your cybersecurity team on how to use the new automation tools effectively and ensure they understand the impact on their roles and responsibilities.
Tips for Ensuring a Smooth Transition to Automated Security Processes
- Start with pilot projects to test the automation tools in a controlled environment before rolling them out across the entire cybersecurity infrastructure.
- Monitor the implementation process closely and address any issues or challenges that arise promptly to prevent delays or disruptions.
- Communicate regularly with stakeholders, including IT teams, cybersecurity experts, and management, to ensure everyone is informed and aligned throughout the transition.
- Document the implementation process and create a knowledge base for troubleshooting common issues and maintaining the automated security processes effectively.
Measuring the Effectiveness of IT Automation Tools in Cybersecurity Operations
- Define key performance indicators (KPIs) to measure the impact of automation on cybersecurity processes, such as incident response time, threat detection rates, and cost savings.
- Utilize analytics and reporting tools provided by the automation platforms to track and analyze the performance of the automated security processes.
- Regularly review and evaluate the KPIs to identify areas for improvement and optimization in the automation tools and processes.
- Seek feedback from the cybersecurity team and other stakeholders to gather insights on the effectiveness of the automation tools and make necessary adjustments for better results.
Wrap-Up
As we conclude our exploration of Effective IT automation tools for cybersecurity, it becomes evident that automation serves as a crucial ally in the ongoing battle against cyber threats. By integrating automation seamlessly into security operations, organizations can bolster their defenses and respond swiftly to potential breaches.
Stay vigilant, stay automated, and stay secure.
Essential Questionnaire
What are IT automation tools in the context of cybersecurity?
IT automation tools in cybersecurity are software applications that enable the automatic execution of tasks to enhance security measures, such as monitoring network traffic, detecting anomalies, and responding to threats.
How does automation reduce human error in cybersecurity operations?
Automation reduces human error in cybersecurity by standardizing processes, eliminating manual intervention in repetitive tasks, and ensuring consistent application of security protocols across systems.
Why is scalability important in automation tools for cybersecurity operations?
Scalability is crucial in automation tools for cybersecurity as it allows organizations to adapt to changing security needs, accommodate growth, and efficiently manage security tasks across expanding infrastructures.